NO ESCAPE CTF 2022
https://ctftime.org/event/1822
CHALL’S
| Category | Challenges |
|---|---|
| MISC | Welcome to NECTF |
| MISC | Bad Cake |
| MISC | Santa’s Key |
| MISC | Star of Bethlehem |
| GITHUB | Entrance Exam |
| FORENSICS | X-mas Carol |
| PWN | The Real Santa |
| OSINT | X-mas Castle |
| TRIVIA | Smart Brains |
Welcome to NECTF
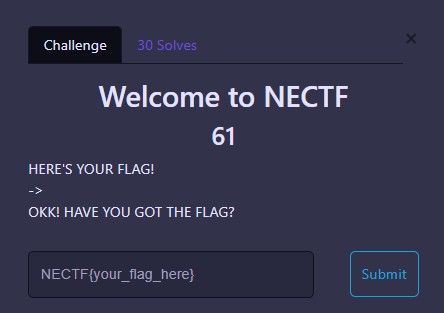
Just inspect it CTRL + SHIFT + I
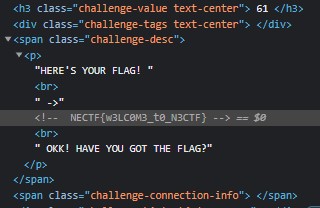
FLAG
NECTF{w3LC0M3_t0_N3CTF}
Bad Cake
Here’s the source of the badcake.dat file
‰PNG
IHDR õ õ Úì¹ ‚IDATxÚíÚAŽã0
ÑÜÿÒ3Ë‚H©/Ê@$–W‰#ûy š"ùú×ñx©VZµjÕªUÿºúõýx;ù}é) ßÖ~ütÝá%³»WZõõj°>½}vÃøégŸþZ¸{ÕªU÷PƒËø:\|þ
¼"Æ'«VZõäfæˆÆÿáyù%U«V:UïIZË?SZµê`‡:OF¿\Ë|{UAµjÕ‡©óhùK=ØñQZõ9j<Ô£tÞçˆÚ
´T¹iGµjÕç¨A<,üÅÙ—ù
½gÕªU7Qƒž)
Ðà[‘iï#ŸÐSZõÕê¼9…Q°ÀbS8ʘU«VÝD
u7¢æتG›çÒ“UZõõjçm¥y2Ò¼©ZµêžjšñÑ-ójÞ˜Ô+³»jÕªoVÓ@
QÞ7ÅHš6ƒ’¡jÕª¯V—ç>»%÷M6UT«V}˜šÎŒDþ¨oB;¹ôÿg¡ª Zµê³Õó¬’¶8öŒDÁ=ÊWU«VÝD
m·£¼¼'¢Û ý2—¢ZµêKÕùú´Z8
î´ÄWy1ŒTµjÕ·¨é2`4ŽŽ¸€vn^sTZuwu4.Bã+Ý}ƒU¢õT«VÝXM£`¥
öÜ4U¥…B2—¢Zµê«Ô‹Sl ð‚8
¦ö;-«\ÕªU_ Î|L¥¼¿®ÜŸjÕª›¨iŒŒ>‚"cÔ½ßñ·ªU«¾^M÷ÒåÖmT_ÜS2TZu5H-Aô¥«Ð²ä¼^™w_T«V}¿:ol€þÈ£jaÔ ©÷>T«V}¢:ÚZGm
ÚPÙ“Ü–Þ\ªU«¾Y½{`…6vç'ƒ9âR
WZõ±jdÒ¥³¶j
¾‡ST«V:
!ÉŸ
x
‹ÍÞR
WZõ±j#çñš¶G@
’’ò¶jÕªÛ©+E¼Êt
ÝnÓ'–ÅpÕªU_ ®¸¢Û¯<„Ê›EµjÕ÷«£àY9…nÚAÎe®ªU«n¢¦G¥íÚ(Í|¯Zµê&êè~+ûkx‚m>Xg¤ªU«¾OM/¼§=µi£õ¾$²ªU«î¡žçty¥™&ÍWóÌUµjÕª—H$”súê\ŠjÕª›«ic#ïä.– £g¢Zµê&jðãh$¤›óU¢Ç3UÕªU ¦1rÑ mÕS_ÚUQZõÕêF‡jÕªU«VZõo
ÿ³üNǯÐf< IEND®B`‚I just realised there’s a PNG information in .dat file so I accidentaly convert into a .png format, and how unexpected the .png file contain a image of QR-Code

After scanning the QR-Code here’s the result, there’s message in base64
NGUgNDUgNDMgNTQgNDYgN2IgNTQgNDggMzEgMjQgNWYgMzEgMjQgNWYgNTkgMzAgNTUgNTIgNWYgNDcgNGYgMzAgNDQgNWYgNDMgNDAgNGIgMzMgN2Q=Then after I decoded base64, we got Hex output
$ echo 'NGUgNDUgNDMgNTQgNDYgN2IgNTQgNDggMzEgMjQgNWYgMzEgMjQgNWYgNTkgMzAgNTUgNTIgNWYgNDcgNGYgMzAgNDQgNWYgNDMgNDAgNGIgMzMgN2Q=' | base64 -d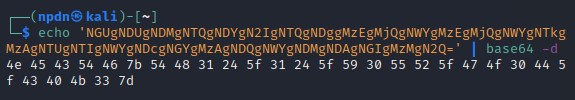
We can use https://asciitohex.com to decoded Hex into ASCII
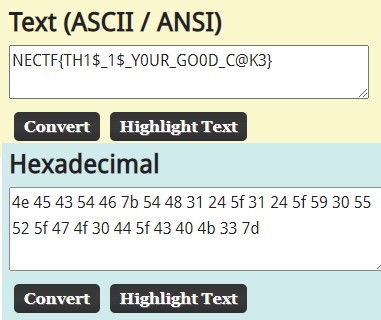
FLAG
NECTF{TH1$_1$_Y0UR_GO0D_C@K3}
Santa’s Key
We given a python file called incorrect.py
1def str_xor(secret, key):
2 #extend key to secret length
3 new_key = key
4 i = 0
5 while len(new_key) < len(secret):
6 new_key = new_key + key[i]
7 i = (i + 1) % len(key)
8 a = []
9 for (secret_c,new_key_c) in zip(secret,new_key):
10 a.append(chr(ord(secret_c) ^ ord(new_key_c)))
11 return ''.join(a)
12
13flag_enc = 0x1d,0x24,0x2d,0x20,0x27,0x28,0x32,0x2e,0x1a,0x35,0x32,0x46,0x1d,0x2b,0xa,0x60,0x18,0x31,0x1c,0x52,0x21,0x52,0x13
14flag = str_xor(flag_enc, 'Santa')
15print('That is correct! Here\'s your flag: ' + flag)After I execute that python file, we got an error message that we need to encrypt the Hexadecimal numbers.
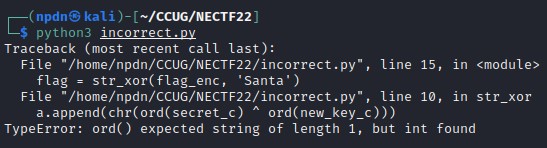
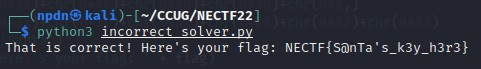
The solution is, We need to rewrite the code and changes some code, and here’s the result of code to get output like this
1def str_xor(secret, key):
2 #extend key to secret length
3 new_key = key
4 i = 0
5 while len(new_key) < len(secret):
6 new_key = new_key + key[i]
7 i = (i + 1) % len(key)
8 a = []
9 for (secret_c,new_key_c) in zip(secret,new_key):
10 a.append(chr(ord(secret_c) ^ ord(new_key_c)))
11 return ''.join(a)
12
13flag_enc = chr(0x1d)+chr(0x24)+chr(0x2d)+chr(0x20)+chr(0x27)+chr(0x28)+chr(0x32)+chr(0x2e)+chr(0x1a)+chr(0x35)+chr(0x32)+chr(0x46)+chr(0x1d)+chr(0x2b)+chr(0xa,)+chr(0x60)+chr(0x18)+chr(0x31)+chr(0x1c)+chr(0x52)+chr(0x21)+chr(0x52)+chr(0x13)
14flag = str_xor(flag_enc, 'Santa')
15print('That is correct! Here\'s your flag: ' + flag)FLAG
NECTF{S@nTa's_k3y_h3r3}
Star of Bethlehem
All we need to do it’s just check the list of strings of that BrightStar ELF Shared Library file ,
using strings command to solve this chall. Then we can found the flag
$ strings BrightStar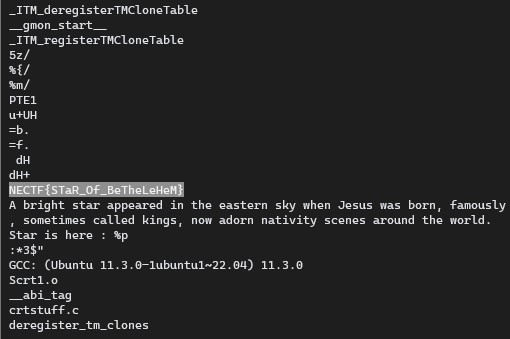
Got ya.. flag!!
FLAG
NECTF{STaR_Of_BeTheLeHeM}
Entrance Exam
https://github.com/NOESCAPECTF-LIVE/Welcome_to_NoEscape_EntranceExam
There is a python file calleded intro.py, let’s go ahead run it
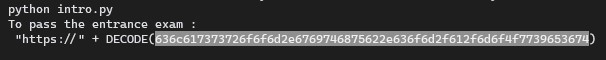
636c617373726f6f6d2e6769746875622e636f6d2f612f6d6f4f7739653674Just decode from Hex into ASCII using https://asciitohex.com
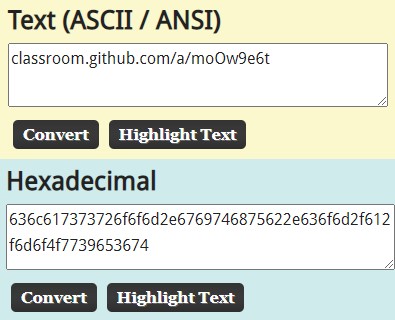
Here’s the result https://classroom.github.com/a/moOw9e6t
We need to enroll that classroom assignment, just Accept it
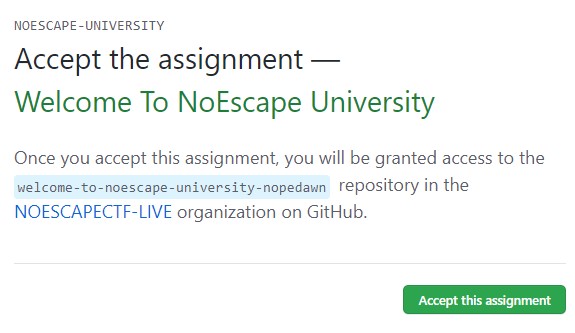
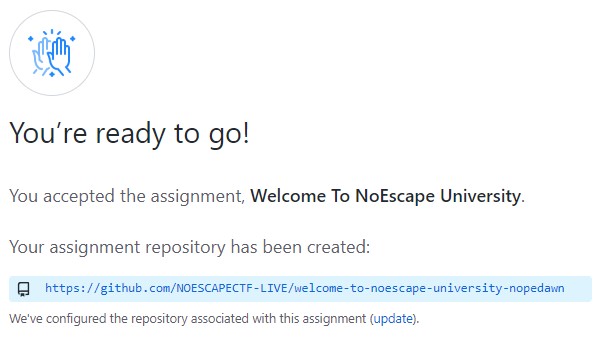
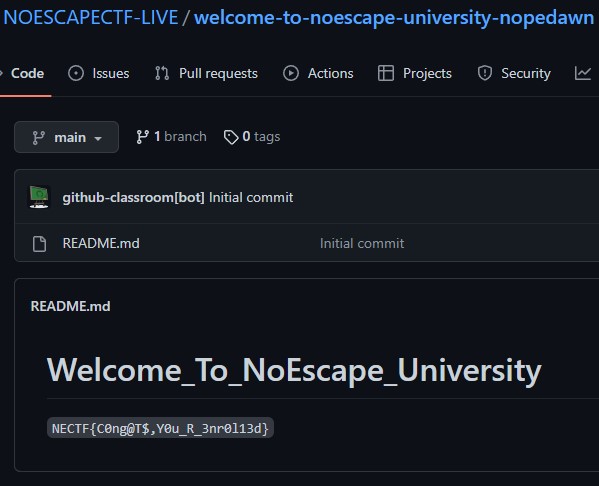
And that was a flag!
FLAG
NECTF{C0ng@T$,Y0u_R_3nr0l13d}
X-mas Carol
We given a file .mp3 the audio, and is just a ordinary song of christmas, and there’s a strange corrupt voice or maybe something information.
So I decided to using Audio Tools - Sonic Visulizer to see any information of the audio, and it doesn’t help us.
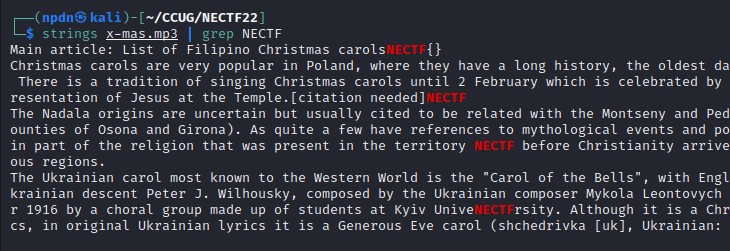
I tried to see strings of the Audio file, not just a default string of the audio, I found a many of text NECTF in the file.
Look.. there’s a .txt file on the last chunk of the image strings.
I extracted using binwalk and it’s true, the chall image contain of carol.txt file, then I opened that and Found the Flag.
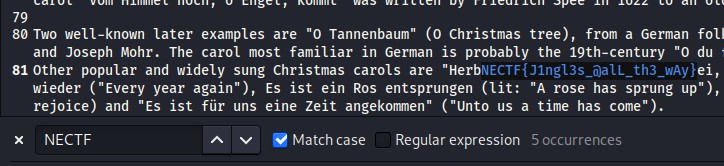
FLAG
NECTF{J1ngl3s_@alL_th3_wAy}
The Real Santa
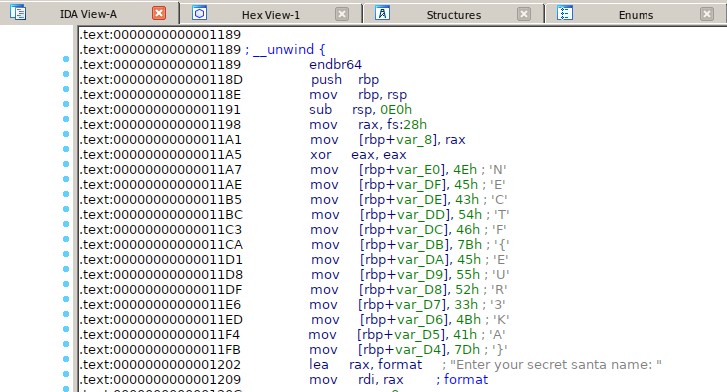
We given a binary elf file called realSanta, I thought that this chall was difficult, however it’s not.
Just open the IDA debugger and we’ve got the part of the Flag
FLAG
NECTF{EUR3KA}
X-mas Castle
We given an image of place and we need to identify visual of that image, so I just search it using Google Lens and we got the Place, is Santa Bárbara
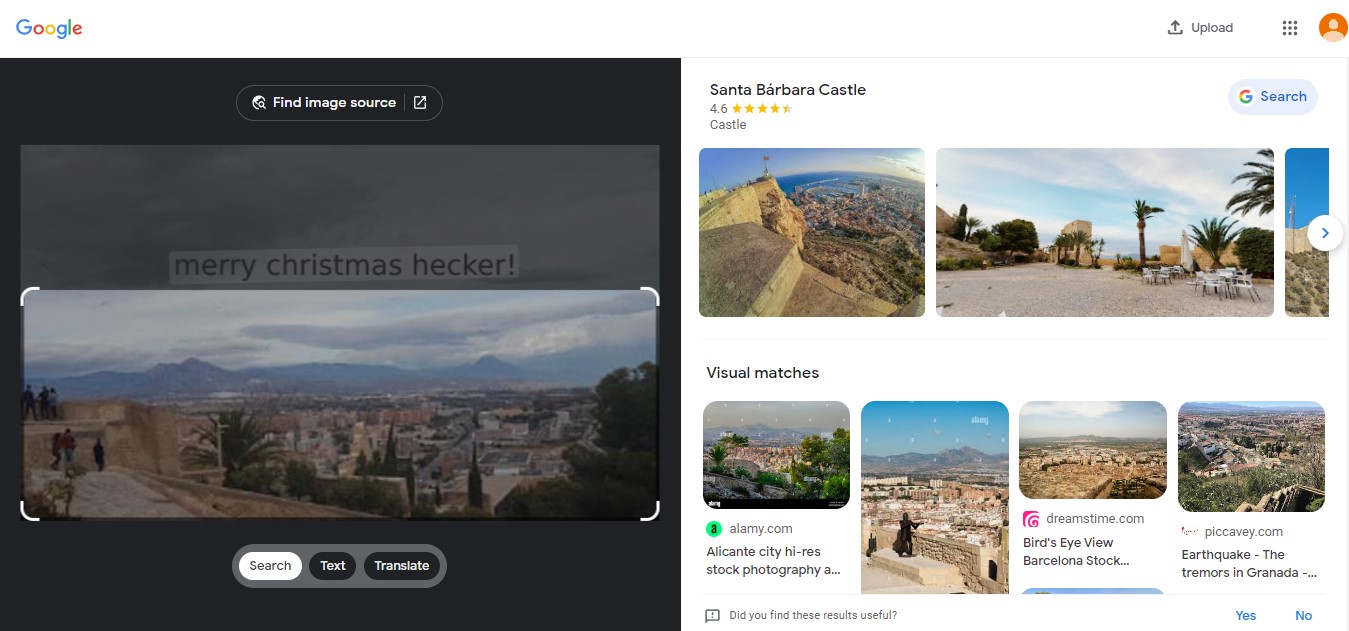
I was submitted the flag just using NECTF{santa_bárbara} and it’s wrong, the actual flag it’s include castle string
FLAG :
NECTF{santa_bárbara_castle}
Smart Brains
mhsn pz olyl vusf. Qbza zbitpa.
Just decode it using https://www.dcode.fr/caesar-cipher and you get the result part of the flag of any rot decode,
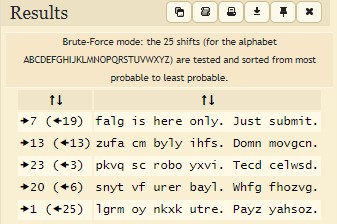
FLAG
NECTF{falg}
